So, how important are cyber-security, internet safety and ensuring your law firm has adequate procedures in place to safeguard against threats? The answer is very important. There are many studies that analyse different data, each giving different answers that vary slightly but are all consistently shocking in terms of data security.
Consider the following key points that have been published on https://www.gov.uk, last updated in July 2022, and realise that the numbers are likely to get scarier as time progresses.
39% of UK businesses identified a cyber-attack in 2022
In case you don't think this number is high enough, let's highlight the keyword in this sentence, ‘identified’. There is almost, with complete certainty, other attacks that have happened, are happening, and will continue to happen in the future that will not be identified, even with the most sophisticated defence software, things will fall through the cracks.
83% of those attacks were phishing attempts
What is phishing you ask? It’s defined as “a method of using social engineering, attempting to deceive people into pretending to be someone else to reveal sensitive information or even going so far as to attempt the target user(s) into installing malicious software to perform actions such as information reconnaissance, data stealing and destruction of device software”.
I don't know how to break it to you, but I’m just going to come out and say it. GDPR is important, data theft is scary and reputation damage leads to loss of clients. All things your law firm wants to be avoiding.
Furthermore, due to technological advances, the bad guys are continuing to improve upon their knowledge and capabilities and for these reasons, it is important that you have a strong defence, so I ask you...
…in the philosophical words of Guns n' Roses, “Where do we go now, where do we go?”
While you can take some steps using technology to your advantage which will be covered later in this blog post, one thing that people often overlook is this:
The starting point to a lot of cyber-attacks is, as you have seen above, through phishing.
So, you may ask, in what situations that the bad guys have won, has made them be successful?
The answers?
It depends...not helpful I know, but I can identify two key takeaways (not the Deliveroo kind) that I see commonly from analysing these types of attacks and spotting the patterns, and they very much go hand in hand.
- Impersonation
- Psychological manipulation
Take, for example, the image below, which took me less time to create than it would to locate a farm, find a lamb, and shake its tail.
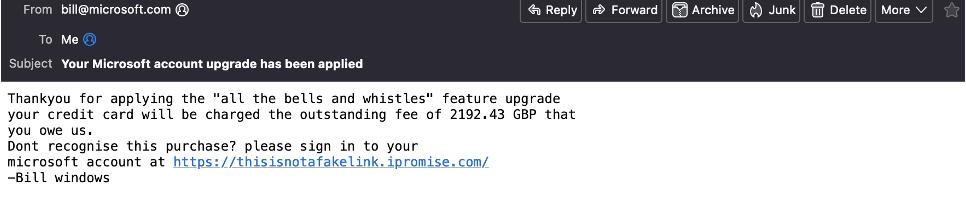
So how do law firms step up their game?
While there are some additional things that you can add to email that can help enhance (or make your life more difficult for many, complicated reasons that deserve a whole book on why) known as SPF, DKIM, DMARC and SMIME, the easy way is to not trust email out of the gate. This is because no matter how you set your email security up, someone else will do it differently to you and something absolutely will clash at some point.
My recommendation is to be suspicious of emails - is what they're asking for really something you'd send through an email that could be intercepted and stolen? Is it something they should have access to anyway?
The bigger question here, really, is how do we establish trust between two parties? The short answer is not to use email as a medium for communication, but that’s not the world we live in, therefore, it’s better to arm ourselves with the knowledge and security defences in the first instance.
There are no ‘one-size fits all’ approaches for email security, it is important to have email as an option, for contacting clients, business to business and for internal use. However, technology is changing and so is the way that we communicate, this puts us in a great position to be able to mix and match multiple communication platforms, this has a two (or more) fold advantage:
- Attackers would have to gain access to the underlying infrastructure (at which point it’s too late) or multiple platforms to impersonate someone.
- It allows you to communicate with the party that “made” the request to confirm its authenticity across separate software solutions.
Here are a few communication channels to consider, that increase the options for clients and can potentially increase the range of choice for confirming someone is who they say they are, when combined.
- Email including web forms
- Live web chat
- Phone lines
- Slack
- And, if you are more security & privacy conscious, Telegram and Signal.
So, what are the key takeaway points summarised?
Email cannot be fully trusted and trying to enhance its security becomes a game of “how many emails are we willing to accept the loss for” of which the answer should be “none” because this could lose you genuine business.
Look for emails that seem suspicious, is Jen from Marketing asking for the password to the website, the full card number, and the pin code and for you to snail mail the company vehicle key to some random postal address? Either that’s not Jen, or you need to go and congratulate her for finally passing her driving test! (don't be rude now).
Establishing multiple communication channels, not only increases the ways that clients can engage with you, it gives you multiple different ways to confirm authenticity with a recipient. For example, at Conscious if David our MD is asking Vaida our Finance Manager anything to do with finance/money e.g. pay a bill, then two they need to communicate in different channels e.g. email and Slack, or Slack and WhatsApp.
We don’t mean to scare you, but it’s better to be safe than sorry! If you have any further questions about email security, speak to your IT team or technology providers.
Remember, your IT team have to be ‘right’ every time. The bad people only have to be ‘right’ once.

